Cybersecurity Solutions
Protect Your Business with Next-Generation Cybersecurity Solutions
In today’s digital world, cyber threats are no longer an “if” but a “when.” From phishing attacks to ransomware and data breaches, businesses of every size face evolving risks that can disrupt operations, compromise sensitive information, and damage reputations.
Our Cybersecurity Solutions are designed to defend your organization with a 360-degree security framework—combining proactive threat detection, rapid response, and continuous monitoring. With us, your business stays one step ahead of hackers and compliant with global security standards.

Cybersecurity Solutions Highlights
Advanced threat intelligence
Advanced threat intelligence provides in-depth, contextualized information about the motivations, capabilities, and tactics of threat actors, enabling organizations to understand and proactively defend against sophisticated cyber threats beyond what basic threat data can offer
Endpoint & network security
Endpoint & network security refers to a layered defense approach protecting both individual devices (endpoints) like laptops and smartphones, and the broader network infrastructure from cyber threats.
24/7 monitoring & incident response
Advanced threat intelligence provides in-depth, contextualized information about the motivations, capabilities, and tactics of threat actors, enabling organizations to understand and proactively defend against sophisticated cyber threats beyond what basic threat data can offer
Compliance with GDPR, HIPAA, ISO standards
Endpoint & network security refers to a layered defense approach protecting both individual devices (endpoints) like laptops and smartphones, and the broader network infrastructure from cyber threats.
Solutions & Features
Our Comprehensive Cybersecurity Offerings:
Why Choose Cybersecurity Solutions for Your Business?
Data Protection: Prevent unauthorized access to sensitive business and customer information.
Business Continuity: Minimize downtime and keep operations running during security incidents.
Reputation Security: Build customer trust by proving your systems are safe and compliant.
Cost Savings: Avoid costly penalties, lawsuits, and operational losses from data breaches.
Regulatory Compliance: Stay ahead of GDPR, HIPAA, PCI-DSS, and ISO security requirements.
Future-Ready Security: Scale your protection as new threats emerge.


Network Security
Firewalls, intrusion detection, and advanced monitoring to safeguard your IT infrastructure.

Endpoint Protection
Defend laptops, desktops, and mobile devices from malware and ransomware attacks.

Identity & Access Management (IAM)
Ensure the right people have the right access, with multifactor authentication and privileged access controls.

Email & Web Security
Block phishing, spam, and malicious URLs before they reach your employees.

Compliance & Risk Management
Meet industry regulations and minimize compliance risks with tailored frameworks.
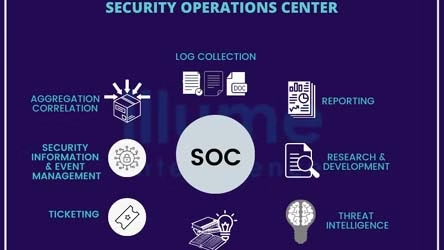
Security Operations Center (SOC) Services
24/7 monitoring, log management, and incident response by certified security experts.

Data Encryption & Backup Security
Protect sensitive data with encryption protocols and secure backup strategies.
Why Choose Us
Your Trusted Cybersecurity Partner
We believe cybersecurity isn’t just about installing software—it’s about building a culture of security. With our team of certified ethical hackers, SOC analysts, and compliance specialists, we help businesses proactively secure their digital ecosystems.
